In my previous post, I listed a number of the SQL Server 2016 new features. Let’s look at the first one in that list – Always Encrypted.
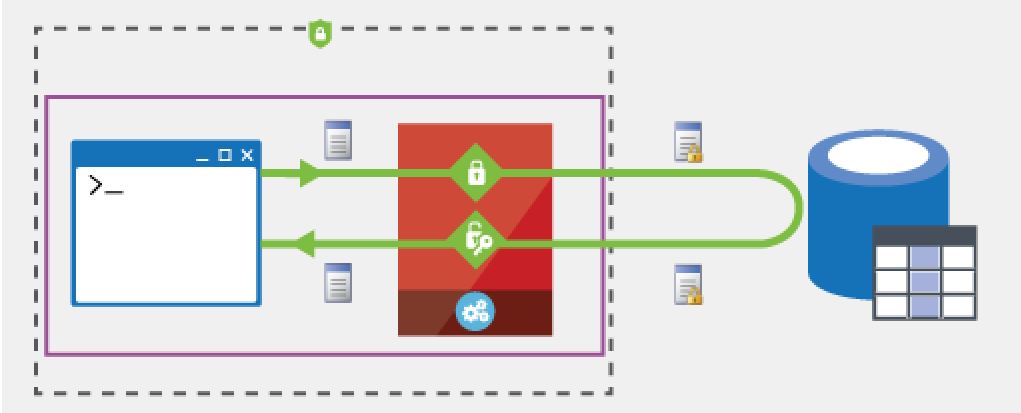
With Always Encrypted the key to unlocking the encryption resides with the application. The encyption key is never passed to SQL Server.
God like administrators cannot view the data on the server in its unencrypted form. This provides a clear separation between the data managers and the data owners as to who can actually see the sensitive data. In this case, the data owners can view the data as they own the applications.
There are two types of encryption :
- Deterministic Encryption – where the same plain text value is stored in the column, the encrypted value will be the same. This allows grouping, filtering and joining by encrypted values but can expose patterns in the encryption which could open up opportunities for guessing what the values are beneath. The probability of successfully guessing values increases when the number of unique values is small.
- Randomized Encryption – the opposite. Randomized encryption values makes the data more secure from pattern guessing however grouping, filtering and joining become impossible to do with any accuracy.
I’ve got the key, I’ve got the secret…..
The Always Encrypted Keys used by the applications come in two types :
- Column Encryption Keys – these keys are used to encrypt sensitive data in columns and all values in a column can use the same key. Encrypted values of those keys are stored in system catalogs and it’s advised to have a secure backup of those keys too.
- Column Master Keys – these keys protect the column encryption keys. They have to be stored in a trusted key store. Information, including location of the master keys is stored in system catalog views.
Who’s driving?
The Always Encrypted Driver does the work between the client and the database to either encrypt or decrypt the data accordingly. This happens transparently without any additional code needed to be added to the application.
How to enable Always Encrypted?
1/ Create a new database and a new table with some columns that you are wanting to encrypt
2/ You can then right mouse click on the database and choose “Tasks->Encrypt Columns”
3/ You’ll be presented with the Always Encrypted Wizard introduction screen, click “Next”
4/ Here you can choose which columns to encrypt, which encryption type and whether to create a new encryption key or use an existing one.
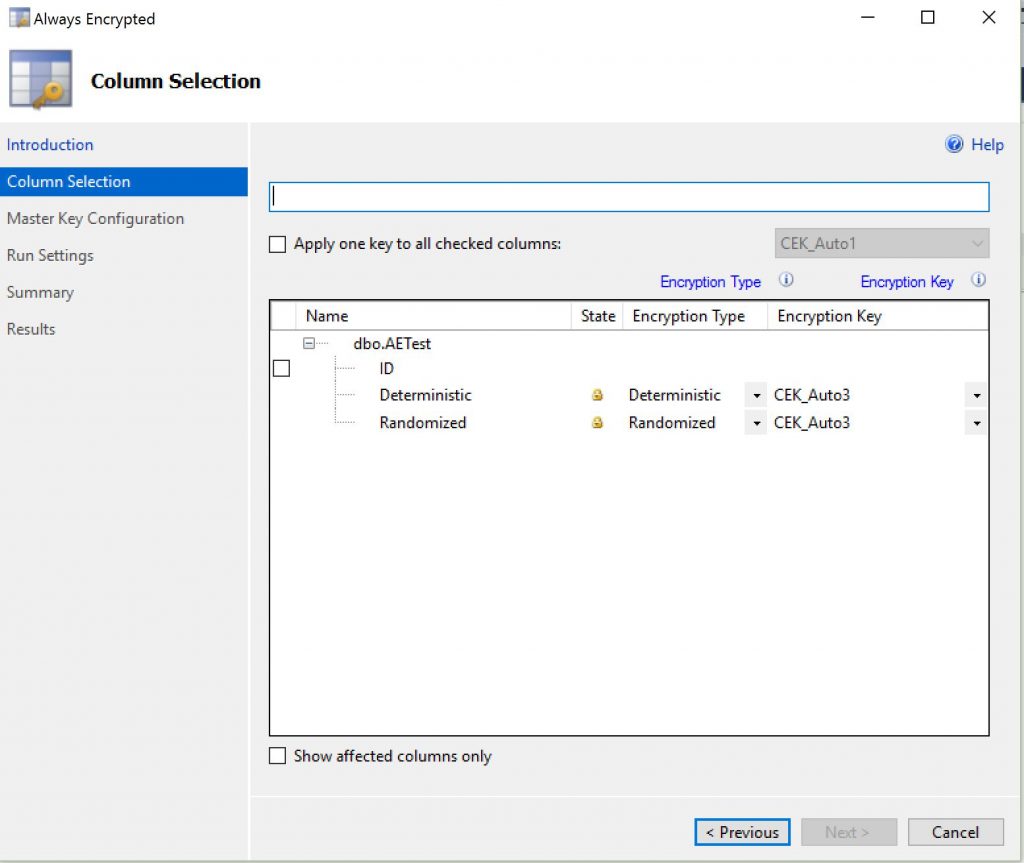
5/ You’ll be presented with the Master Key configuration page where you can choose which column master key to use, where to store it (in a certificate store or in an Azure key vault) and the master key source.
6/ The next screen gives you the option whether to proceed immediately or to create a Powershell script to run it later. Click through and it will do it’s bit and should come back that it has completed.
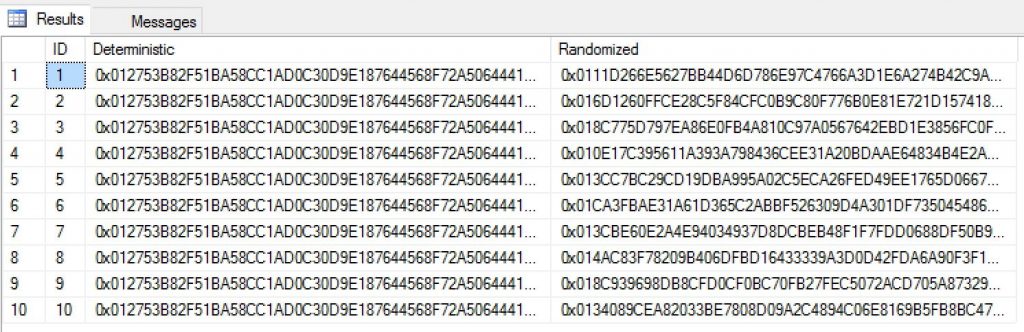
Before I encrypted the columns, I added some data to both the “Deterministic” and “Randomized” columns of my table. 10 rows were added with exactly the same data. The only difference being that the strings were different for each column.
So the data looked like this, added 10 times :
INSERT INTO AETest(Deterministic, Randomized)
VALUES('This is deterministic','This is randomized');
After the encryption, I queried the data to view the encrypted patterns. As you can see the two types of encryption are clearly visible with deterministic returning the same pattern for all 10 rows and random behaving, well, randomly. 🙂

Leave a Reply